The following is a quick guide to setting up an virtual server on Amazon Cloud EC2:
SETUP
1) Login to AWS Management Console using your Amazon account and navigate to EC2
2) In the top right hand corner, check that the location of the servers is the one that you would like to use, I will be using Ireland
3) In the “Getting Started” section of the EC2 dashboard, select Launch instance to create a new virtual server
4) I will be demonstrating the “Classic Wizard”
5) Select the Amazon Machine Image (AMI) that you would like to use, I will be using the Amazon Linux AMI 2012.09, 64bit edition
6) Enter the instance details, I am going to be creating 1 micro instance on EC2 so I’ve not changed any of the options on this page or the following Advanced Instance Options page or Storage Device Configuration page
7) Now you can create tags, using tags for your instances is really useful so I highly recommend it. I’ve set the key and value to “PAWS-router-management-server”
8) Creating a public/private key is vital for using SSH to access your virtual server. Give the private key a sensible name and download it
9) Creating a new security group is highly recommended, otherwise you can use make use the default group. I will be accessing the server using SSH so I’ve opened up port 22 to SHH
10) Review the opinions you have chosen and save
ACCESS
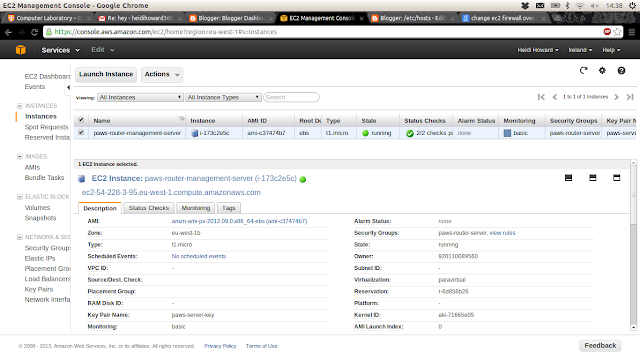
1) If you navigate to the “instances” page, you will now be able to see your newly created instance. Selecting your instance will give you access to more detailed information
2) To access your new instance, open the terminal and locate the private key you downloaded during set up
3) Change the permissions on the key using: $ chmod 400
4) Connect via SSH using: $ ssh -i
More details on the Amazon Linus AMI are available at http://aws.amazon.com/amazon-linux-ami/ . Its useful to note that there is no root password, you can’t SSH in as root or use su but if you use sudo, no password is required and that the package manager used is yum